Known issues and FAQ
Known issues
There are no known issues to report at this time.
Frequently asked questions (FAQ)
How many rules can I have on my site?
You can create a large number of rules. However, the number of active rules at any given time is limited. See Entitlements for details on what is allowed per customer plan.
Can I purchase additional active rules?
No. The number of active rules is fixed based on customer plan. See Entitlements.
How are certain special and escaped characters handled?
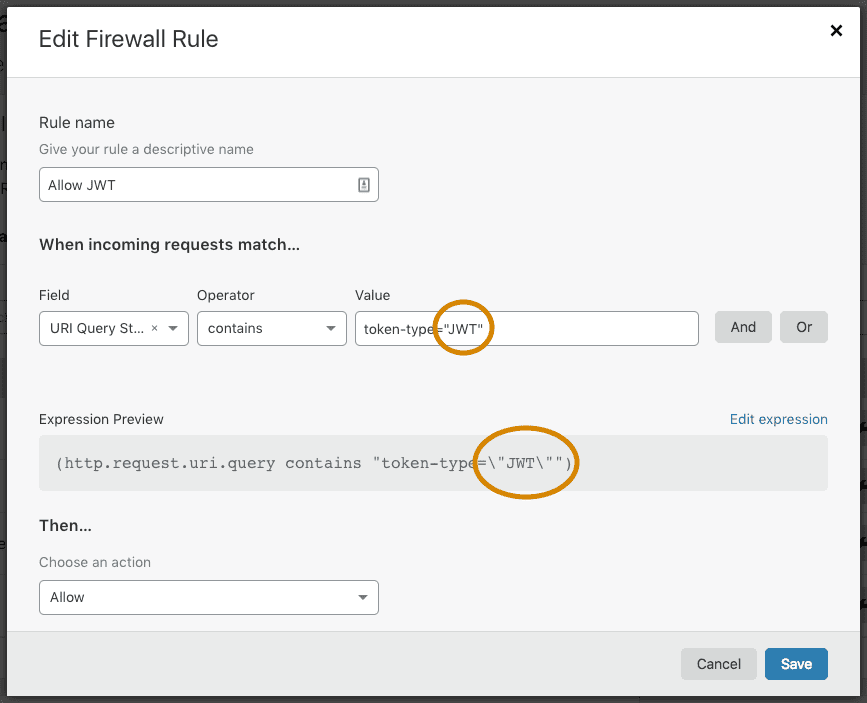
When used as literals in an expression, the backslash \ and double quote " characters require proper escaping.
An expression built using the Visual Expression Editor in the Firewall Rules UI does not require you to manually escape those special characters. Conveniently, the Expression Builder takes care of any necessary escaping in the final expression by automatically prepending a backslash such that \ and " become \\ and \", respectively.
The following image illustrates how double quotes are automatically escaped to \" once they appear in the plain text expression generated in the Expression Editor:
Why isn't my regular expression pattern matching working?
If you are using a regular expression, we recommend you test it against an RE2 testing tool like Regular Expressions 101.
Also, note that http.request.method fields requires all-caps for method names.
How can I use the Threat Score effectively?
The Cloudflare Threat Score is a key item behind the Security Level functionality in the Cloudflare dashboard.
Threat Score as configured by Security Level is based on:
- High - for scores greater than 0
- Medium - for scores greater than 14
- Low - for scores greater than 24
- Essentially off - for scores greater than 49
Enabling a high threat score for sensitive areas, like comment form pages or login forms, can add an effective level of protection. Integrating Threat Score with Firewall Rules is advantageous because you can specify a Captcha vs. a JS Challenge, or even a block. You can also exclude IP addresses using and not logic.
How does Firewall Rules handle traffic from known bots?
Caution about potentially blocking bots
When you create a firewall rule with a Block, Challenge (Captcha), or JS Challenge action, you might unintentionally block traffic from known bots. Specifically, this might affect search engine optimization (SEO) and website monitoring when trying to enforce a mitigation action based on URI, path, host, ASN, or country.
See How do I create an exception to exclude certain requests from being blocked or challenged?
Bots currently detected
The table below lists known bots that Firewall Rules currently detects. When traffic comes from any of these bots, the cf.client.bot field is set to true.
| Bot | Description |
|---|---|
ahrefs | Ahrefs SEO bot |
apple | Applebot is the web crawler for Apple, for products like Siri and Spotlight Suggestions |
archive.org | Archive.org bots |
baidu | Baidu search engine bots |
better uptime | Bot for monitoring website uptime |
bing | Bing search engine bots |
feedbin | Feedbin.com bots |
Google search engine bots | |
grapeshot | Grapeshot (Oracle) SEO bots |
LinkedIn bots | |
mail.ru | Mail.ru bots |
naver | Naver (South Korean) search engine bots |
pingdom | Pingdom.com monitoring bots |
Pinterest bots | |
seznam | Seznam search engine bots |
sogou | Sogou search engine bots |
uptimerobot | Uptime Robot monitoring bots |
yahoo | Yahoo! search engine bots |
yandex | Yandex search engine bots |
How do I create an exception to exclude certain requests from being blocked or challenged?
There may be situations in which you want to enforce a blocking or challenging action but make exceptions for specific types of requests.
Cloudflare supports two methods to permit requests through Firewall Rules expressions:
- Exclude a type of request from being blocked or challenged, for example based on IP address, ASN, or country
- Create an independent firewall rule with an Allow action
If you wish to permit certain exclusions, the examples below illustrate a few possible approaches.
Example 1
Exclude multiple IP addresses from a blocking/challenging rule that assesses Threat Score
| Basic rule, with no exclusion | |
| Action | block (or challenge) |
| Expression | (http.host eq "example.com" and cf.threat_score > 5) |
| Rule that excludes IP addresses from being blocked/challenged | |
| Action | block (or challenge) |
| Expression | (http.host eq "example.com" and cf.threat_score > 5) and not (ip.src in {1.2.3.4 4.3.2.110.20.30.0/24}) |
| Two rules to allow exceptions and block the rest | |
| Rule 1 | Action: allow Expression: ip.src in {1.2.3.4 4.3.2.110.20.30.0/24} |
| Rule 2 | Action: block (or challenge) (http.host eq "example.com" and cf.threat_score > 5) |
Example 2
Block Amazon Web Services (AWS) and Google Cloud Platform (GCP) because of large volumes of undesired traffic, but allow Googlebot and other known bots that Cloudflare validates
| Basic rule, with no exclusion | |
| Action | block (or challenge) |
| Expression | (ip.geoip.asnum in {7224 15169}) |
| Rule that excludes known bots that Cloudflare validates | |
| Action | block (or challenge) |
| Expression | (ip.geoip.asnum in {7224 15169}) and not cf.client.bot) |
| Two rules to allow exceptions and block the rest | |
| Rule 1 | Action: allow Expression: cf.client.bot |
| Rule 2 | Action: block (or challenge) Expression: (ip.geoip.asnum in {7224 15169}) |
Why does a Firewall Event display a Cloudflare IP address even though other fields match the client details?
This happens when a request goes through a Cloudflare Worker.
In this case, Cloudflare considers the client details, including its IP address, for triggering security settings. However, the IP displayed in the Firewall Events will be a Cloudflare IP address.