Actions
Overview
Actions tell Cloudflare how to handle HTTP requests that have matched a firewall rule expression.
Supported Actions
The table below lists the actions available in Firewall Rules. These actions are listed in order of precedence. If the same request matches two different rules which have the same priority, precedence determines the action to take.
For example, the Allow action takes precedence over the Block action. In a case where a request matches a rule with the Allow action and another with the Block action, precedence resolves the tie, and Cloudflare allows the request.
The only exception to this behavior involves the Log action. Unlike the other actions, Log does not terminate further evaluation within Firewall Rules. This means that if a request matches two different rules and one of those rules specifies the Log action, the second action will be triggered instead, even though Log has precedence. Although Firewall Rules would not trigger the Log action in this case, Firewall Analytics would still record the hit as an “additional match.”
| Action | Description | Order of Precedence |
| Log |
| 1 |
| Bypass |
| 2 |
| Allow |
| 3 |
| Challenge (Captcha) |
| 4 |
| JS Challenge |
| 5 |
| Block | Matching requests are denied access to the site. | 6 |
Choosing Actions in the Rule Builder
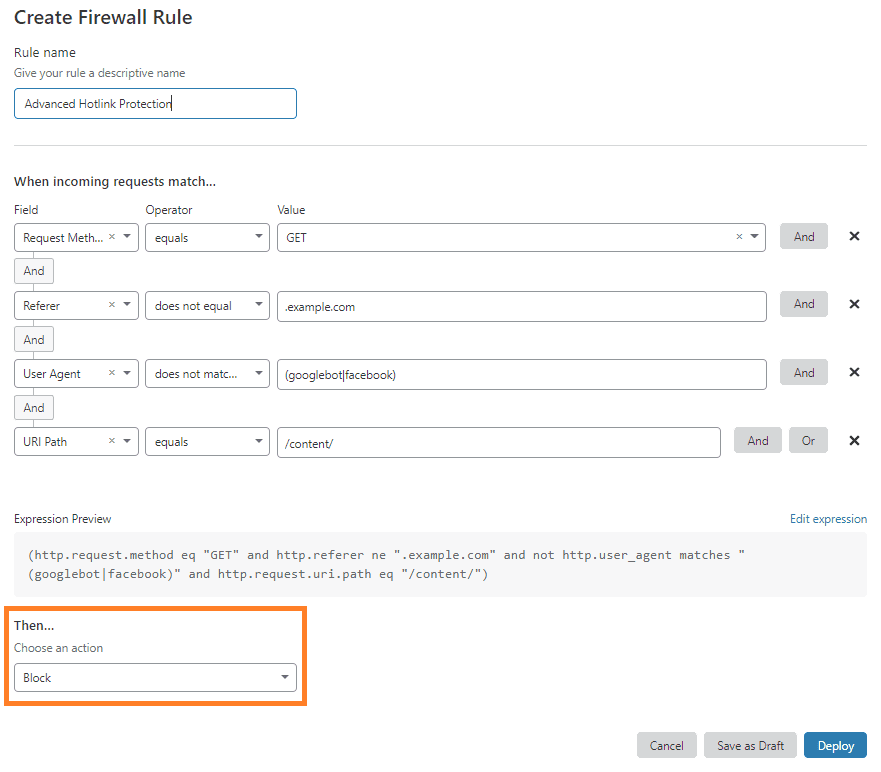
Choosing an action in the Cloudflare Expression Builder is simple. After naming a rule and building your expression, pick the appropriate option from the Choose an action drop-down list. In this example, the chosen action is Block:
For more on building firewall rules in the Firewall App, see Create, edit, and delete rules.