Create an API Shield™ rule
Use the API Shield interface in the Cloudflare dashboard to create a firewall rule that requires requests to your API or web application to present a valid client certificate.
Before you can create an API Shield rule, you must do the following:
After you have created your API Shield rule, configure your mobile app or IoT device to use your Cloudflare-issued client certificate.
Use the API Shield Rule interface
To create an API Shield rule in the Cloudflare dashboard, follow these steps:
Log in to your Cloudflare account Home page and click the zone containing the host you want to protect with API Shield.
The Cloudflare dashboard displays.
Click the Firewall app.
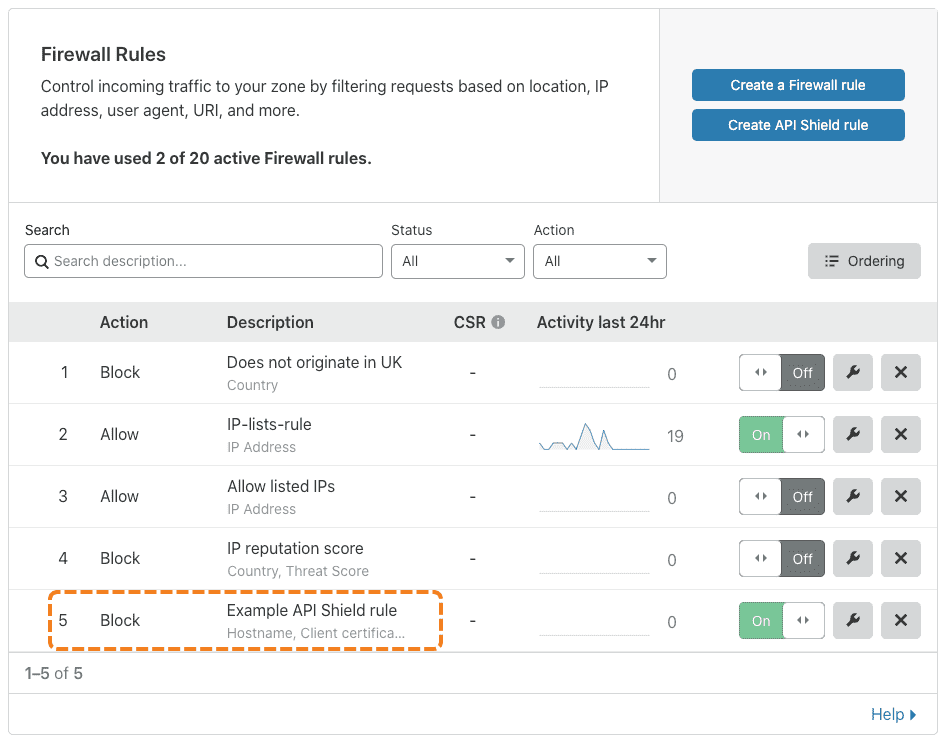
The Firewall Overview displays.
Click the Firewall Rules tab.
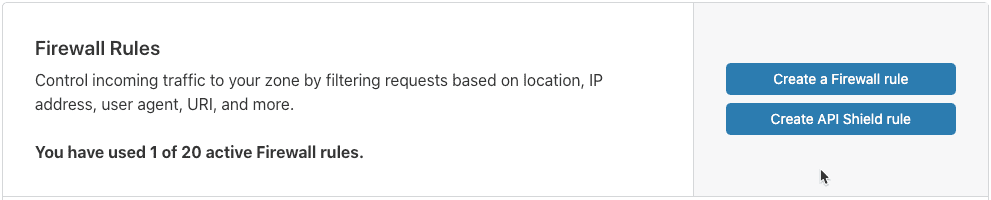
The Firewall Rules card displays.
Click Create API Shield rule.
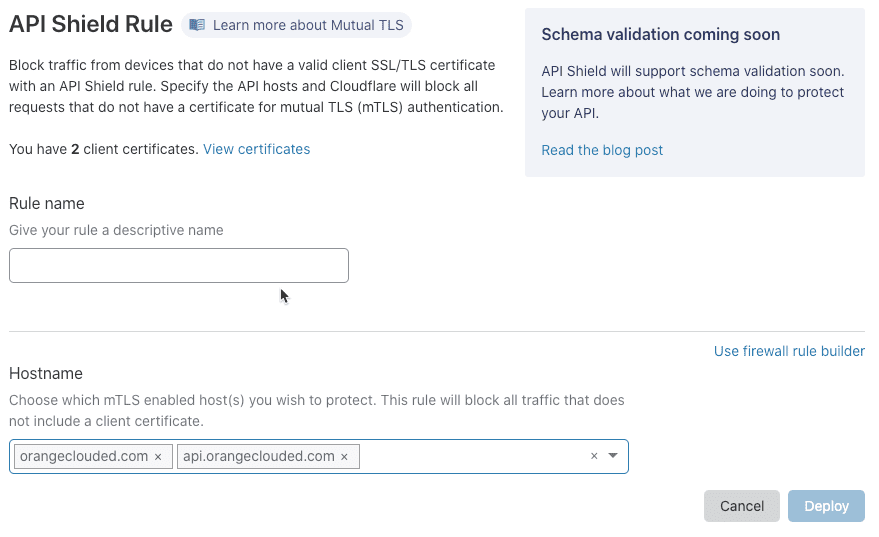
The API Shield Rule dialog displays.
Enter a descriptive identifier for your API Shield rule in the Rule name input.
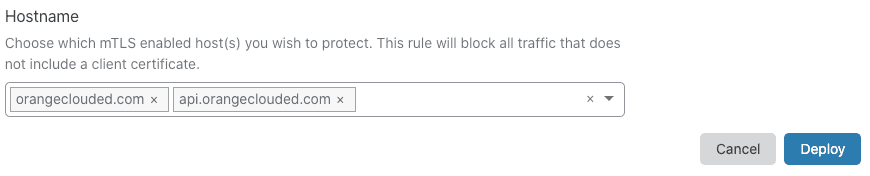
To select the hosts you want protect with you API Shield rule, use the Hostname input. By default, all available hosts are listed. Only hosts in the zone you selected in Step 1 and for which you enable mTLS are available. To remove a host from the rule, click the associated X icon.
To create your rule and make it active, click Deploy.
The API Shield Rule dialog closes and the Firewall Rules card displays with your new rule in the list.
Once you have deployed your API Shield rule, configure your mobile app or IoT device to use your Cloudflare-issued client certificate.
Review your rule in the Expression Builder
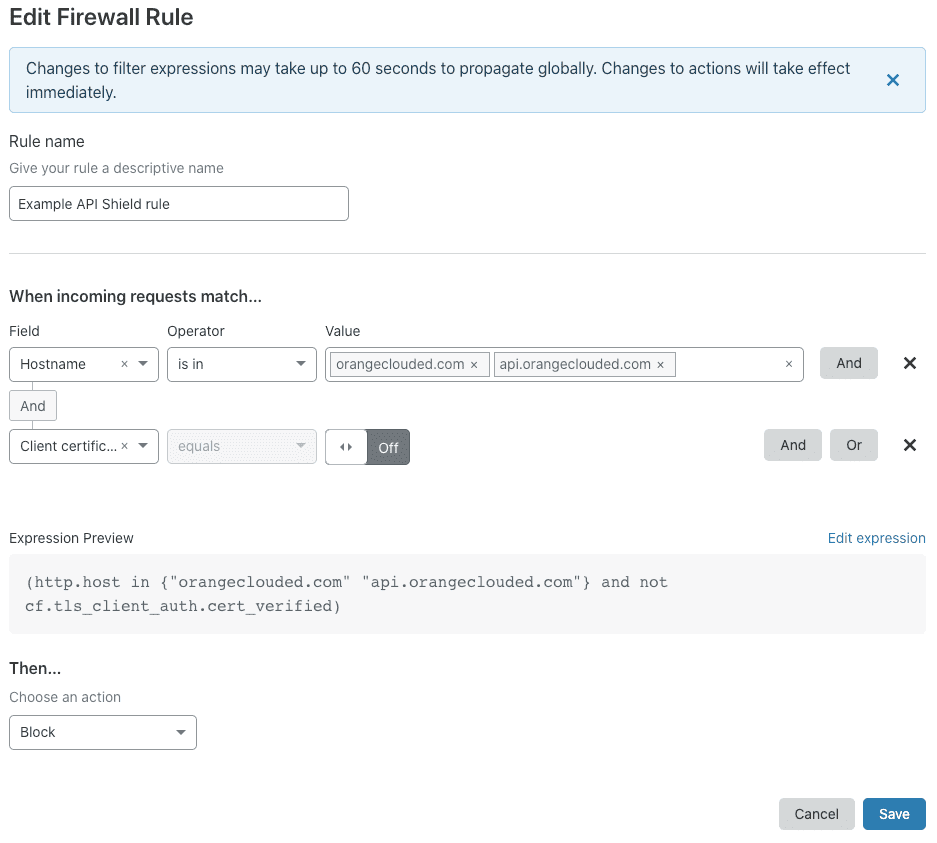
To review your API Shield rule in the Firewall Rules Expression Builder, click the wrench icon associated with your rule.
The Edit Firewall Rule dialog displays, and the Expression Builder's visual interface renders your API Shield rule:
Note Expression Preview. Your API Shield rule includes a compound expression formed from two simple expressions joined by the and operator.
The first expression uses the http.host field, combined with the in operator, to capture the hosts your API Shield rule applies to.
The second expression—not cf.tls_client_auth.cert_verified—returns true when a request to access your API or web application does not present a valid client certificate.
Because the action for your rule is Block, only requests that present a valid client certificate can access the specified hosts.